Cyber security solutions must be applied as part of a holistic approach that includes standards, people, processes, procedures, and technologies.
In the industrial sector, accident risk reduction and essential services continuity depend on the proper functioning of the automation and control systems identified by the acronym IACS, Industrial Automation and Control Systems. Therefore, cyber security involves the measures taken to protect IACS systems from accidental threats or intentional attacks. IACS systems are currently more accessible and vulnerable to attacks than in the past due to the massive deployment of computing and connectivity platforms that allow data exchange with other systems and external networks.
In this scenario, the application of health and safety standards and risk assessment processes in the workplace (HAZOP) and in the industrial process (PHR) are not sufficient to address cyber security threats to IACS systems, as they do not consider the possibility of simultaneous events, the understanding of the attacker's strategies, and the possible loss of fundamental services. Essentially, cyber security threats cannot be ruled out based on traditional risk assessment processes. It is critical that cyber security solutions implement an IACS system.
Standards
IEC 61511 standard on safety instrumented systems (SIS) for the process industry, updated to the second edition, requires that a security risk assessment (SRA) be carried out to identify safety vulnerabilities in the SIS. With reference to cyber security for the OT and IACS world, there are three other standards related to safety: IEC 62443, ISO/IEC 27001, and ISA TR84.00.09.
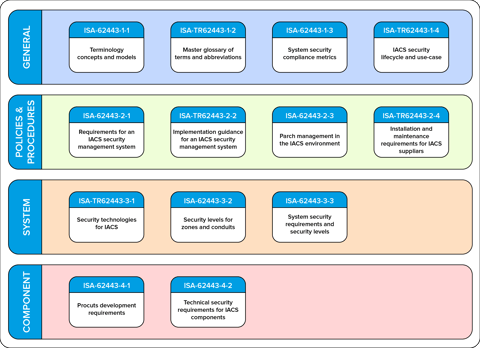
IEC 62443 is a set of standards developed by the ISA99 committee, and internationally recognized, that specifies process and product requirements for the development of Industrial Automation and Control Systems (IACS). IEC 62443-2-1 establishes general policies of a Cyber Security Management System (CSMS). IEC 62443-4-1 (process) and IEC 62443-4-2 (product) standards were created to encourage the purchase of products and systems from suppliers who can ensure the safety for every system component, and at all stages of the application lifecycle. Other important standards are ISO/IEC 27011 for telecommunications, ISO/IEC 27017 for cloud computing, and ISO/IEC 27019 for the energy sector. These are examples where, compared with the requirements of ISO/IEC 27001 (the international reference standard for information security management systems), additional controls have been added to meet different protection needs.
Digital security in industrial networks (DNV)
Zones and conduits
Assessing the most significant cyber attacks to IACS systems in recent times, in addition to the technical skills of the hackers, we can see the willingness to cause damages not only to digital infrastructures, but also to physical infrastructures and people. The rise of new threat and attack mechanisms has completely changed the operation of industrial IACS, SIS and Scada systems. Threats to these systems can come from the Internet, external networks, maintenance activities, software updates, IIoT devices, and unauthorized access.
Once all IACS assets have been identified, they must be organized into zones and conduits (IEC/TS 62443-1-1). The definition of the number of zones and how assets are grouped must be accomplished on a case-by-case basis, considering relevant factors such as size and scope of the IACS system, criticality level compared to the process, system geographic position or logical location, access mode, business standards, and assets managers.
Zones should be defined in a hierarchical structure that allows to devise a defensive architecture. Assets grouping into zones is intended to minimize the need for real-time data communications, so that each zone is self-sufficient in applying appropriate countermeasures (e.g., network segregation) without compromising operations, as done by implementing physical or logical subnets called DMZs (DeMilitarized Zones).
Path Management
Even in the context of IACS, it is useful to point out that safety and (cyber)security underlie different concepts. The former deals with protection from accidents and failures. The "security" deals with protection from cyber attacks.
A "security vulnerability" is specifically referred to vulnerable software problems. Threat management is a process used by cyber security professionals to prevent cyber attacks and respond promptly to security incidents. The introduction of Attack Path Management tools can be considered precautionary. This approach allows the graphical representation of possible attack paths, enabling an understanding of where vulnerabilities exist and what steps a malicious user may use to exploit gaps in the system.
Cyber security operational management
Cyber security is focused on protecting computer systems and digital information from internal and external attacks. However, incidents occur even with the adoption of the best technologies, and cyber attack risk is never equal to zero because human and organizational aspects are important.
In 2016, the global functional safety standard IEC 61511 was updated to include two requirements regarding cyber security for a SIS. The first requirement asks that a Security Risk Assessment (SRA) be performed to identify cyber vulnerabilities. The second requires that SIS project provides the necessary resilience against identified cyber security risks. However, these requirements are not sufficient, so that the IEC 62443 standard for industrial control system security becomes relevant. On the other hand, users need a good framework, and for this reason the Process Hazards Analysis (PHA) becomes relevant. PHA is a detailed cyber security risk assessment methodology for IACS and SIS, compliant with the ISA/IEC 62443-3-2 standard. Furthermore, from the combination of the IEC 61511 and IEC 62443 standards, two levels of safety arise: Safety Integrity Level (SIL) and Security Level (SL), which must interact in risk analysis and ensure a high degree of overall safety. SIL is defined as the level of risk reduction provided by a Safety Instrumented Function (SIF) in Functional Safety management in the process industry. Security Level represents the confidence level of vulnerability degree of an IACS (developed and validated according to IEC 62443 standard) from malicious attacks.
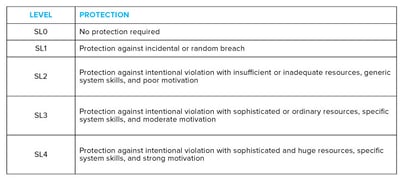 Security Levels
Security Levels
Would you like to know more? Watch our webinars "IACS Cyber Security and Functional Safety, combined risk reductoin requirements" and "IACS Cyber Security - Avoiding common misconceptions" in our YouTube channel.


